

as i understand it, the money goes to the foundation, and it’s the corporation that develops the browser. so it’s probably not strictly forbidden, but it does imply that the money is not for browser development.


as i understand it, the money goes to the foundation, and it’s the corporation that develops the browser. so it’s probably not strictly forbidden, but it does imply that the money is not for browser development.
in the health sector specifically, IT is a mess because you can’t stop people from working or there will be deaths. one thing you should take away from this is that their jobs are important and it is crucial that they can do them. it is your job to support them; anything that stops them doing their job or makes it take longer, even once, is dangerous. improving infra for its own sake is not a good idea because it comes at the risk of peoples lives. the details don’t matter in the face of that.
if this stresses you out, you can absolutely change jobs. i did.
if you think you can work within those parameters, and you think you can find ways to improve the system in-place while mitigating the risks, then you will be highly respected.


mozilla takes donations, but they don’t fund Firefox development with that money. that’s usually what you’re home against it.


sweden.
and I went back to check, it was imported by a costume shop in collaboration with hard rock cafe in the early 90s but the decision from the board of business to encourage people to spend for this holiday came in 97.


halloween was imported into this country by a costume shop in 1997. this is common knowledge and the shop itself is very proud of this fact. because of this it is an explicitly consumerist holiday, and it is younger than me by a good margin. i do not know anyone who celebrates.


deleted by creator
on the internet everything is true. therefore if you don’t preface your thoughts with “CW: opinion” your writing permanently alters reality and people will be angry at you for inconveniencing them.
imho.


don’t use balenaetcher, it’s a terrible piece of software. use unetbootin or usbimager.
*gestures vaguely at the world in general*


with proper application of sisu, it will open in both directions


deleted by creator


In north america, yes. i have municipal water, i’ve stayed in hotels all over europe, and i’ve never had the feeling of drowning in a pool when drinking tap water before going over there. the worst thing i’ve encountered in europe is filtered tap water, which tastes like charcoal but is drinkable. the chlorinated water just made my throat close instinctively.


everything is chlorinated. i get painful rash if i ingest chlorinated water, so basically everything was undrinkable. this was also true for soft drinks the time i visited Vegas, so my options for hydration were extremely limited.
chicken, peanuts, curry powder, banana. no pineapple.
that or the classic lyxkebabpizza (with fries), or maybe a good calskrove.
well speech-dispatcher has no synthesis component, you can plug in any tts engine that follows the interface. it’s nice to have a choice in engine just by implementing the support. personally i use piper which i feel gives a pretty good performance.
i believe that’s what speech-dispatcher is; a uniform interface for tts systems.


yakety sax is based on a song with lyrics! “yakety yak” by the Coasters
shouldn’t there at least be an option to use speech-dispatcher?


the reporter is a real asshat, judging by their twitter.
first:
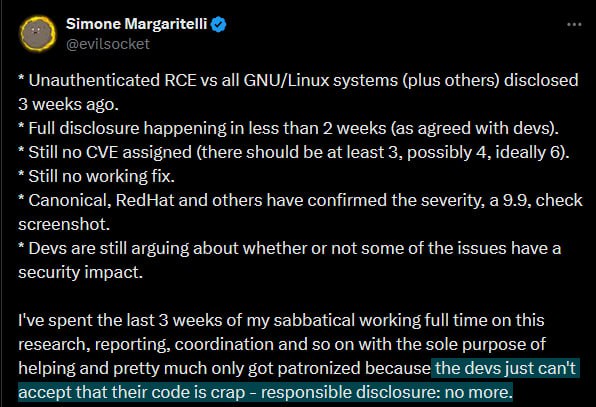
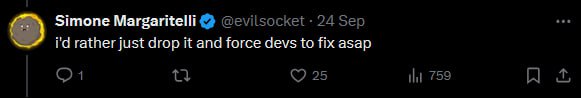
then, later:
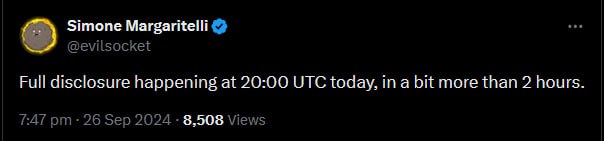
i can chime in with some actual experience!
my current problems with KDE are
and what’s fun about this is, the issues are so intermittent and random that i never know what i’m going to get on a given day!